Identity Cloud service instance endpoints
Your Identity Cloud service instance is identified by its custom_name.
The custom name must be unique and may contain only lower case letters (a-z) or digits (0-9). Underscore (_) or hyphen (-) cannot be used.
IP address
Ubisecure will assign a public IP address for your Identity Cloud service instance:
- Your service endpoint public IP address (provided by Ubisecure)
Domain name
You can either choose the default (custom_name.onubisecure.com) domain or use your own domain name managed by the customer:
- Ubisecure managed DNS (default)
- Customer managed DNS and mail server
Ubisecure managed DNS
If your Identity Cloud service instance has the default Ubisecure managed DNS, it will be reachable at the following addresses:
| URI | Network access control | Description |
|---|---|---|
| https://login.custom_name.onubisecure.com/uas | Public | SSO authentication service endpoint |
| https://login.custom_name.onubisecure.com/cdc | Public | SSO Common Domain Cookie service endpoint |
| https://login.custom_name.onubisecure.com/password | Public | SSO password change UI |
| https://manage.custom_name.onubisecure.com/ubilogin | Authorized source addresses specified by customer | SSO management UI – System management console for administrative users only |
| https://manage.custom_name.onubisecure.com/sso-api | Authorized source addresses specified by customer | SSO API endpoint |
| https://manage.custom_name.onubisecure.com/otpserver | Authorized source addresses specified by customer | One-time password (OTP) server |
| https://account.custom_name.onubisecure.com/eidm2/wf/admin | Authorized source addresses specified by customer | CustomerID management UI |
| https://account.custom_name.onubisecure.com/eidm2/services | Authorized source addresses specified by customer | CustomerID old API endpoint |
| https://account.custom_name.onubisecure.com/customerid-rest/services | Authorized source addresses specified by customer | CustomerID new API endpoint |
| https://apps.custom_name.onubisecure.com/application_path | Public and/or authorized source addresses specified by customer | Optional custom applications (none unless otherwise agreed) |
Ubisecure provides the mail services (SMTP) for Ubisecure managed DNS. No action is required on the customer's part.
Customer managed DNS
With customer managed DNS, all the above URI addresses will have a different host name as given by the customer.
If your Identity Cloud service instance has customer managed DNS, the customer is responsible for managing the following public DNS Resource Records (RRs):
| NAME | TYPE | RDATA | Description |
|---|---|---|---|
| login.custom_name.example.com | A | Your service endpoint public IP address provided by Ubisecure | SSO authentication service endpoint |
| manage.custom_name.example.com | CNAME | login.custom_name.example.com | SSO management UI |
| account.custom_name.example.com | CNAME | login.custom_name.example.com | CustomerID management UI |
| apps.custom_name.example.com | CNAME | login.custom_name.example.com | Optional custom applications (none unless otherwise agreed) |
Customer may choose all the above host names freely under the customer's domain. Use of the custom_name is optional in customer given host names. Any valid host names ( RFC-1123) under the customer's domain can be used.
Customer mail server
With customer managed DNS, the customer is responsible for providing an SMTP server for the Identity Cloud service instance:
- SMTP host name
- Port (usually 465 or 587)
- Security protocol (STARTTLS, TLS, SSL)
- User name
- Password
- From-address (default: noreply@example.com)
The customer is responsible for their domain email security configuration and related DNS records such as SPF, DKIM, DMARC, and similar.
Customer managed network security
The Identity Cloud service has robust security policies and procedures in place. The service does not require additional customer managed security measures unless the customer has specific requirements of their own.
The customer is responsible for opening access to the above service endpoints from the authorized source networks.
| Host name | Protocol | Port | Description |
|---|---|---|---|
| login | TCP | 443 | SSO services |
| manage | TCP | 443 | SSO management |
| manage | TCP | 22 | SSH proxy |
| account | TCP | 443 | CustomerID services |
| apps | TCP | 443 | Optional custom applications |
The customer is responsible for enabling access to their provided SMTP service from the following addresses:
| Network address | Protocol | Port | Description |
|---|---|---|---|
| 52.48.241.20 52.49.21.167 52.16.199.125 | TCP | Customer specified (usually 465 or 587) | Identity Cloud gateways (Europe) |
| 52.22.75.180 52.2.149.128 52.70.7.162 | TCP | Customer specified (usually 465 or 587) | Identity Cloud gateways (North America) |
| 52.197.188.87 52.192.82.84 | TCP | Customer specified (usually 465 or 587) | Identity Cloud gateways (Asia-Pacific) |
If special arrangements have been agreed for custom applications, customer is responsible for any relevant configurations at their end.
VPN is available as an additional option on request.
Retrieving service instance logs
You can retrieve your Identity Cloud service instance logs via SFTP.
Customer SSH key pairs
The customer is responsible for managing one or more SSH key pairs for access to the Identity Cloud service instance logs. Send your SSH public keys to Ubisecure for access to the logs:
- Your SSH public key(s)
Keep your private keys secret. Do not send the private keys to Ubisecure or anyone else.
SFTP connection via SSH proxy
1. Add your private key to an SSH authentication agent before connecting. The proxy command uses SSH agent forwarding to authenticate your connection to the log server.
ssh-add
2. The log server will be reachable via SFTP using the following proxy command:
sftp -o "ProxyCommand ssh -W %h:%p %r@manage.custom_name.example.com" monitor@logs # or the old usage # sftp -o "ProxyCommand ssh -A %r@manage.custom_name.example.com nc %h %p" monitor@logs
| Argument | Description |
|---|---|
| sftp | SFTP Secure file transfer program |
| -o | Pass options to SSH |
| ProxyCommand ssh | Specifies the ssh command to connect to the target server. |
| -W %h:%p | Requests that standard input and output on the client be forwarded to the target host and port over the secure channel. These values do not need to be changed. They will be replaced by the ProxyCommand automatically. The %p will be replaced by the default port value 22. |
| -A | Enable forwarding of the authentication agent connection (mandatory) |
| %r | The remote user on the proxy is the same as on the target host. This value does not need to be changed. It will be replaced by the ProxyCommand automatically. |
| manage.custom_name.example.com | Use the host name of your manage service endpoint for the SSH access proxy. |
| nc %h %p | Ncat redirects the connection to the target host and port. These values do not need to be changed. They will be replaced by the ProxyCommand automatically. The %p will be replaced by the default port value 22. |
| monitor@logs | The remote user and target host name. |
Use the SFTP commands to browse the logs on the server.
On Windows using WinSCP and PuTTY
Configure WinSCP to use the Plink and Pageant programs that come with PuTTY.
1. Add your private key to Pageant (SSH authentication agent) before connecting.
2. Connect to log server via Putty:
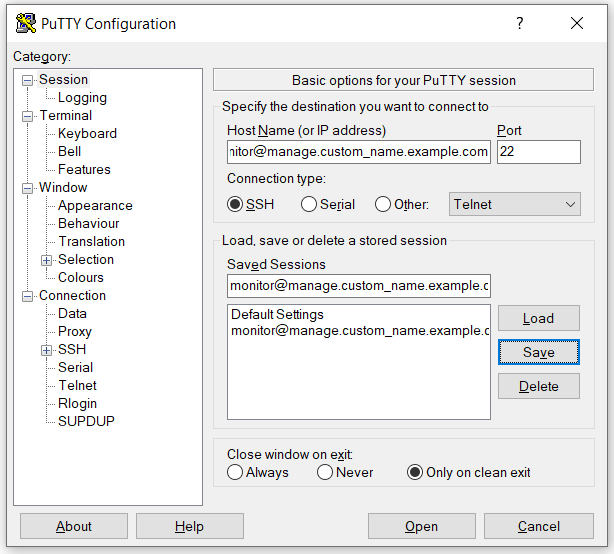
3. The log server will be reachable using the following WinSCP configuration:
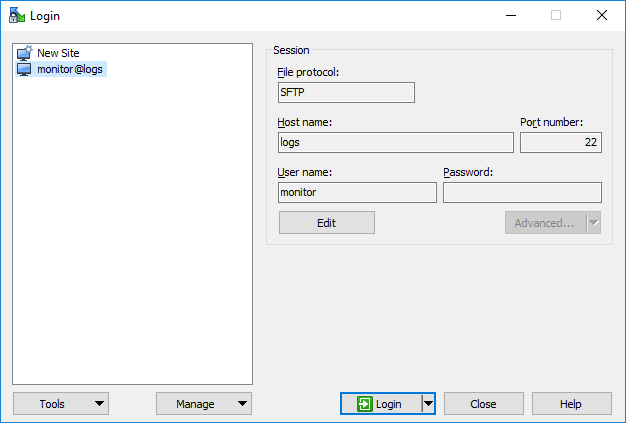
Session / File protocol: SFTP
Host name: logs
User name: monitor
Advanced...
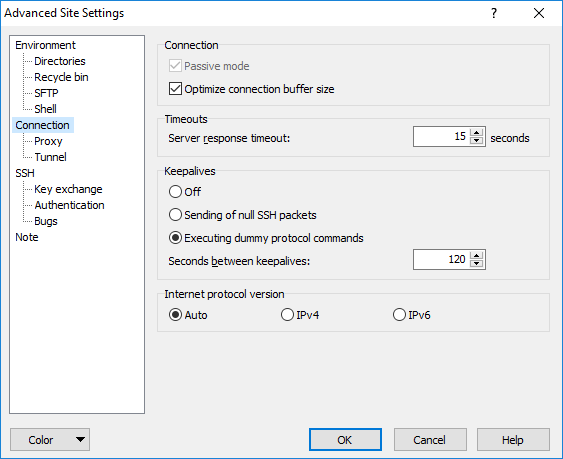
Connection → Keepalives / Sending of null SSH packets
Seconds between keepalives: 120
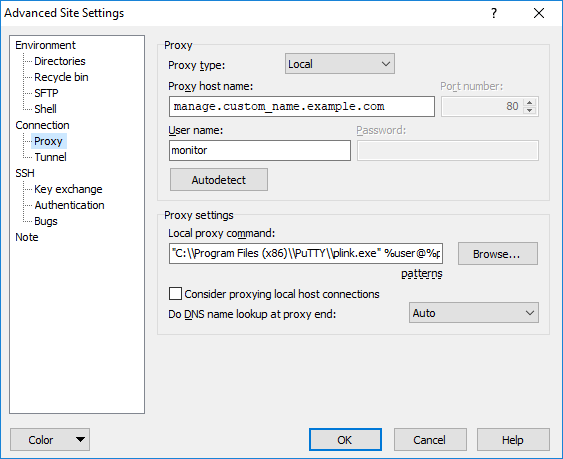
Connection / Proxy → Proxy type: Local
Proxy host name: manage.custom_name.example.com
User name: monitor
Proxy settings / Local proxy command: "C:\\Program Files (x86)\\PuTTY\\plink.exe" %user@%proxyhost -nc %host:%port
Contents