User driven federation with eIDAS authentication
This configuration example is tested with SSO 8.4.0 and CustomerID 5.4.0
In this example we use Suomi.fi authentication portal which gives option to select eIDAS authentication. We want to configure user driven federation to Ubisecure CustomerID so that users can link their eIDAS identity with existing account in CustomerID.
Summary of steps:
- Set up Suomi.fi authentication method
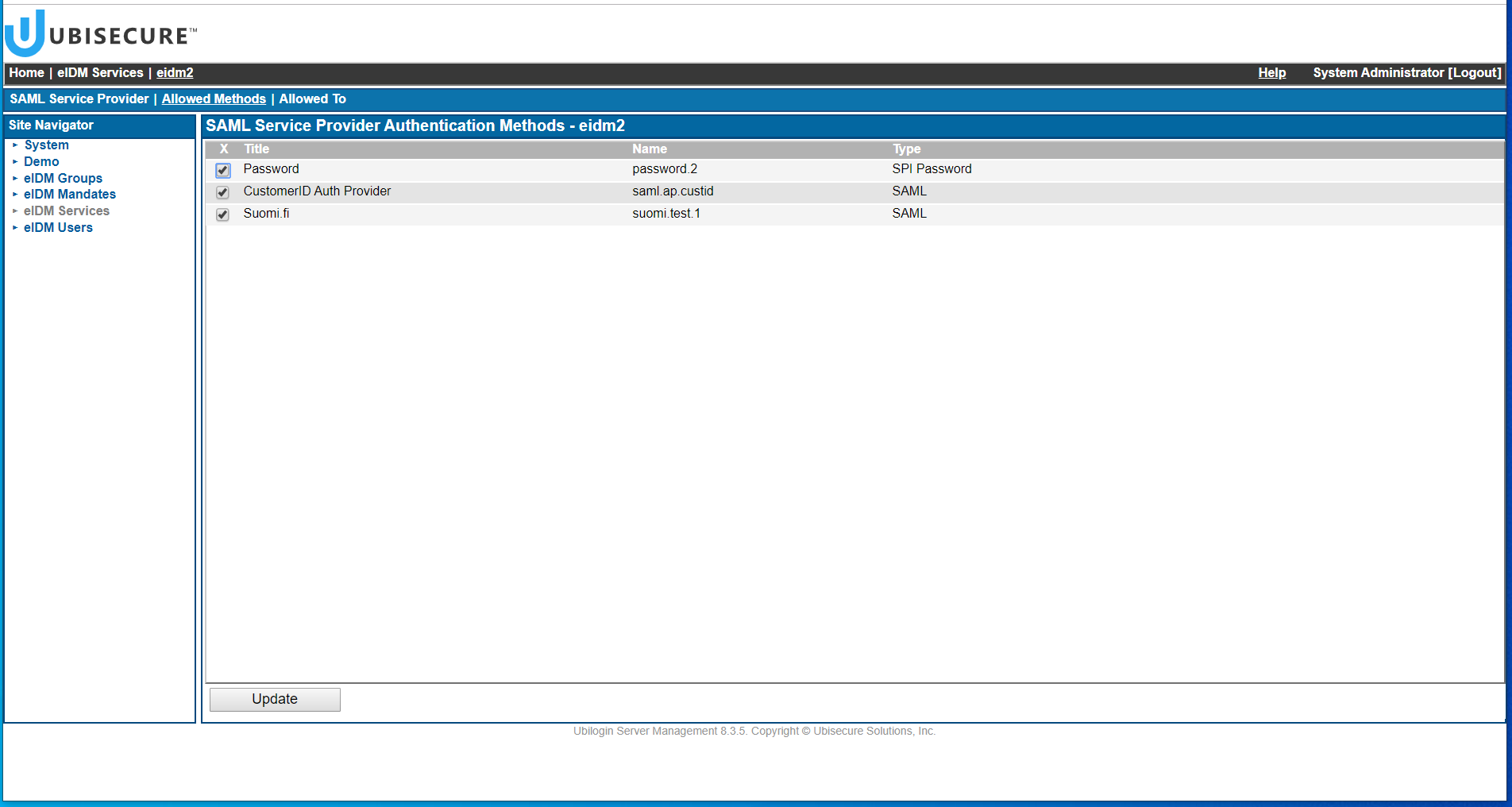
- Enable authentication method for CustomerID
- Set up UDF for SSO login
- Set up UDF for CustomerID registration
- Configure authorization policy
- Create suomiUsers group, add workflow as allowed application and Suomi.fi as allowed method for the group.
- Edit eidm2.properties and protection.properties to enable UDF in CustomerID registration
Details of required configuration:
- Authentication method settings. Note SAML NameID Policy (set X509SubjectName) and Compatibility flag set.
2. Authentication method settings
3. UDF configuration is done following User driven federation - CustomerID documentation. Listing 6 needs to have ubiloginServiceInputParameter modified as below. Suomi.fi sends either PersonIdentifier for eIDAS authentications or urn:oid:1.2.246.21 for other authentication methods. Below we are linking account regardless of which one of the two is returned from suomi.fi.
dn: cn=44a5a6c3-706e-419f-adf8-d31f182bcffa,cn=CustomerID User Mapping,cn=Server,ou=System,cn=Ubilogin,dc=example,dc=com
changetype: add
objectClass: ubiloginServiceUserMappingEntry
objectClass: ubiloginServiceReference
objectClass: top
ubiloginServiceDN: cn=CustomerID Federation,cn=Services,ou=System,cn=Ubilogin,dc=example,dc=com
ubiloginServiceInputParameter: subject ${method['http://eidas.europa.eu/attributes/naturalperson/PersonIdentifier'].isEmpty() ? nameID.format('hetu').nameQualifier('tupas.group').spNameQualifier('tupas.group').spProvidedID(method['urn:oid:1.2.246.21']).value(method['urn:oid:1.2.246.21']) : nameID.format('PersonIdentifier').nameQualifier('eidas.group').spNameQualifier('eidas.group').spProvidedID(method['http://eidas.europa.eu/attributes/naturalperson/PersonIdentifier']).value(method['http://eidas.europa.eu/attributes/naturalperson/PersonIdentifier'])}
The above configuration will only enable UDF linking and logging in if the user already has an CustomerID account, which must be separately linked during the first authentication with the eIDAS method. In the following section we look at how CustomerID should be configured to automatically set up eIDAS authentication for a registered user.
CustomerID registration configuration
Edit authorization policy settings in SSO management for workflow application which handles authentication to registration functions as shown in the following screenshots.
1. Open the workflow application
2. Configure group
SetNameID value is "${method['http://eidas.europa.eu/attributes/naturalperson/PersonIdentifier'].isEmpty() ? nameID.format('hetu').nameQualifier('tupas.group').spNameQualifier('tupas.group').spProvidedID(method['urn:oid:1.2.246.21']).value(method['urn:oid:1.2.246.21']) : nameID.format('PersonIdentifier').nameQualifier('eidas.group').spNameQualifier('eidas.group').spProvidedID(method['http://eidas.europa.eu/attributes/naturalperson/PersonIdentifier']).value(method['http://eidas.europa.eu/attributes/naturalperson/PersonIdentifier'])}"
3. add method and group as allowed for workflow
3. configure registration to CustomerID
registration.1 = person
registration.1.logo.key = admin
registration.1.enabled = true
registration.1.protection.configuration = 1
registration.1.inviteonly = false
registration.1.approval = false
registration.1.mobile.confirmation = false
registration.1.email.confirmation = false
registration.1.organizations= { "path" :"Users" }
registration.1.methods = [ { "name" : "suomi.test.1", "mandatory" : "true", "default" : "true", "visible" : "false"} ]
registration.1.userinfo.fields = firstname, surname, email
registration.1.summary.fields = firstname, surname, email
registration.1.userinfo.optional =
registration.1.use.samlap.with.returnurl = true
protection.1.methods = suomi.test.1 protection.1.sso.template = default protection.1.continue = https://account.example.com/eidm2/wf/register/person protection.1.customeriduseronly = false