Google Apps integration installation and testing - SSO
The installation steps are as follows:
Task | Description |
|---|---|
1 | Review system requirements |
2 | Create account or acquire administrator access to Google Apps Premier Edition or Google Apps for Education |
3 | Configure Ubisecure Authentication Server 5 |
4 | Create Application in Ubisecure SSO Management for Google Apps |
5 | Generate certificate |
6 | Configure Google Apps |
7 | Test |
Installation
Google Apps Account Creation
SSO with Google Apps requires the Premier Edition or Google Apps for Education. A 30 day free demonstration account is available.
Ubisecure SSO Configuration
Google Apps does not sign the AuthnRequest which is sent to Ubisecure SSO. By default, Ubisecure SSO requires that all AuthnRequest messages are signed. To support Google Apps, unsigned AuthnRequest messages must be enabled.
Add the following line to the
<installation directory>\ubilogin\webapps\uas\WEB-INF\uas.properties file:
# saml interoperability features com.ubisecure.ubilogin.uas.saml2.compatibility = AuthnRequestValidate
Redeploy the Ubisecure SSO applications. For a standard installation, use the config\tomcat\update.cmd command:
C:\>cd \PROGRA~1\UBISEC~1\UBILOG~1\ubilogin\config\tomcat
C:\PROGRA~1\UBISEC~1\UBILOG~1\ubilogin\config\tomcat>
C:\PROGRA~1\UBISEC~1\UBILOG~1\ubilogin\config\tomcat>update.cmd
The Ubilogin Server service was stopped successfully.
1 file(s) copied.
524 File(s) copied
The Ubilogin Server service is starting....
The Ubilogin Server service was started successfully.
Create a SAML Application using the metadata shown below. Please refer to the Management user interface - SSO for more details. Modify the text in bold to reflect the hostname used at Google. Copy and paste the metadata when activating the application (refer to Figure 1):
<EntityDescriptor entityID="google.com" xmlns="urn:oasis:names:tc:SAML:2.0:metadata">
<SPSSODescriptor protocolSupportEnumeration="urn:oasis:names:tc:SAML:2.0:protocol">
<NameIDFormat>urn:oasis:names:tc:SAML:1.1:nameid-format:unspecified</NameIDFormat>
<AssertionConsumerService index="1" Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="https://www.google.com/a/ubilogin.ubisecure.com/acs" />
</SPSSODescriptor>
</EntityDescriptor>
If users will access different domains within Google Apps, i.e., multiple Google App accounts will be used with one Ubisecure SSO, activate “Use a Doman Specific Issuer” by selecting the checkbox and modify the entityID in the first line to match the value shown (see Figure 3). This setting is appropriate for service provider type installations.
<EntityDescriptor entityID="google.com/a/ubilogin.ubisecure.com" xmlns="urn:oasis:names:tc:SAML:2.0:metadata">
<SPSSODescriptor protocolSupportEnumeration="urn:oasis:names:tc:SAML:2.0:protocol">
<NameIDFormat>urn:oasis:names:tc:SAML:1.1:nameid-format:unspecified</NameIDFormat>
<AssertionConsumerService index="1" Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST"
Location="https://www.google.com/a/ubilogin.ubisecure.com/acs" />
</SPSSODescriptor>
</EntityDescriptor>
| Figure 1. Importing metadata into SAML Agent |
Set "Allowed to" to all users of unregistered authentication method.
Username must be set to reflect the email address of the user in Google Apps. Username is sent as SAML NameID. For example:
keith.uber@ubilogin.ubisecure.com
Google Apps Account Configuration
Enabling single sign-on (SSO) for Google Apps
To enable SSO for Google Apps:
From the Google Apps Advanced Tools page, select "Set up single sign-on (SSO)".
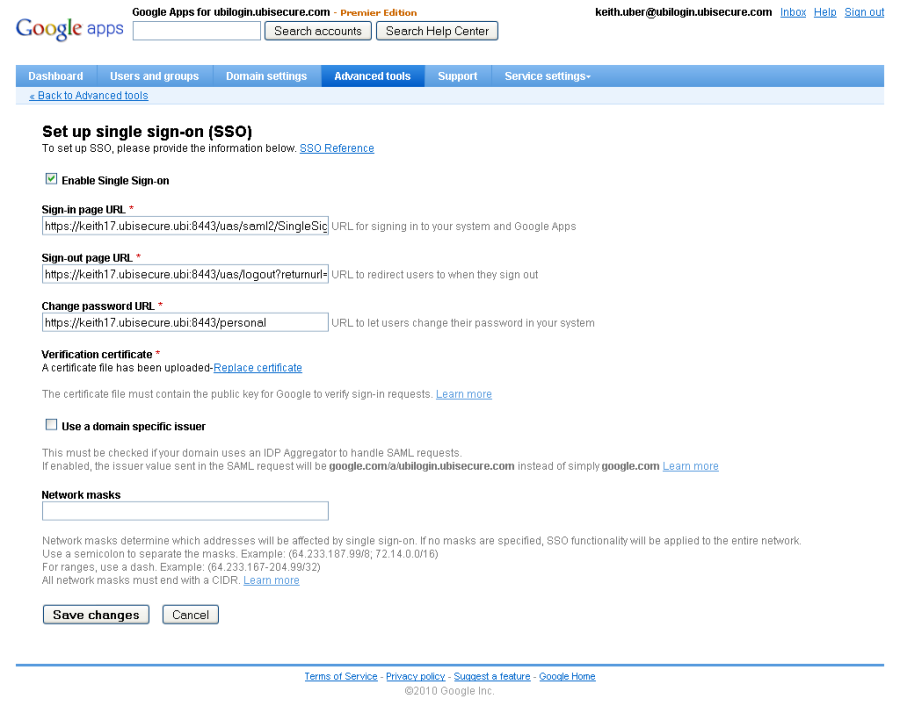
Complete the settings as shown below:
NOTE: In this example, the
uas.urlishttps://keith17.ubisecure.ubi:8443/Replace this value with the
uas.urlvalue fromwin32.configorunix.config.Adding users to Google AppsEnable Single Sign-on
Activate this by selecting the checkbox.
Sign-in page URL (URL for signing in to your system and Google Apps)
Set this value to the location of the Ubisecure SSO service. For example:https://keith17.ubisecure.ubi:8443/uas/saml2/SingleSignOnService
Sign-out page URL (URL to redirect users to when they sign out)
Set this value to the location of the UAS logout link. For example:https://keith17.ubisecure.ubi:8443/uas/logout?returnurl=http://www.ubisecure.com
(Adjust returnurl to match desired page to be shown after sign out.)
Change password URL (URL to let users change their password in your system)
Set this value to the location of your password application. For example:https://keith17.ubisecure.ubi:8443/password
Verification certificate
Upload server public key file in DER format created usingubikt.jartool. To create the public key, execute the following command:java -jar ubikt.jar -ubilogin win32.config|unix.config export - publickey publickey.txt -der
The resulting
publickey.txtfile must be uploaded to Google Apps.
Use a Domain Specific Issuer
Only activate this if more than one Google Apps domain is in use. The Metadata must be modified to include the domain specific EntityID. Please refer to SSO Configuration for instructions.
Network masks
Leave blank to redirect all users from all IP address to Ubisecure SSO for authentication.
To add users to Google Apps:
The username value configured in Ubisecure SSO must be set to reflect the email address of the user in Google Apps. Username is sent as SAML NameID. For example:
keith.uber@ubilogin.ubisecure.com
Add all required users to Google Apps. Use an email address that can be derived from information stored in external user directories or in certificates.
Testing
Login
There are two ways to sign in:
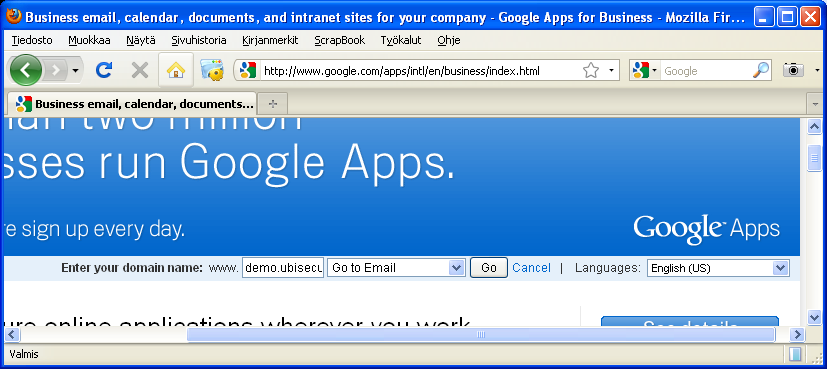
Entering the domain in the main Google Apps login page.
Figure 4. Activating SSO by typing the domain name - Using the URL for a Google App (e.g., mail) containing the domain name, for example:
https://mail.google.com/a/ubilogin.ubisecure.com
Logout
The logout link from within a Google App should initialize the Ubisecure SSO logout sequence and close all open sessions.