Lab 1.3: Authentication Methods
- Basics of Ubisecure SSO authentication methods
- How to configure Ubisecure SSO internal authentication methods
- How to configure authentication via external authentication services (federation)
- SSO and CustomerID installed
Ubisecure Identity Server supports an extensive list of authentication methods. The article Authentication methods - SSO shows how to configure the most common authentication methods.
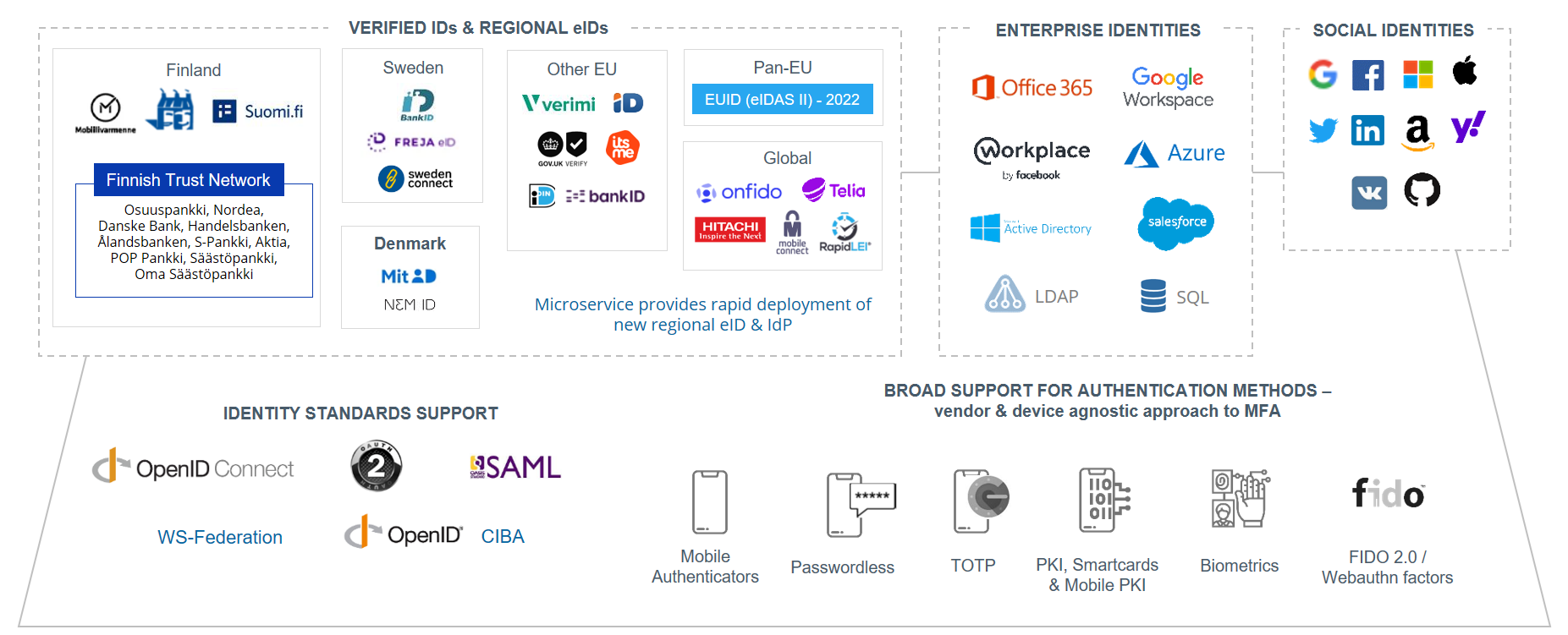
The external authentication methods can be divided into a few main categories: Verified IDs & Regional IDs, Enterprise identities, Social identities, and Stronger assurance methods. Here are some common examples:
During this training session we will work on two of them:
- SMS One-time Password
- Social Login (Google)
Instructions
Part 1: Configuring authentication via SMS One-time Password for MySmartPlan
How SMS OTP works?
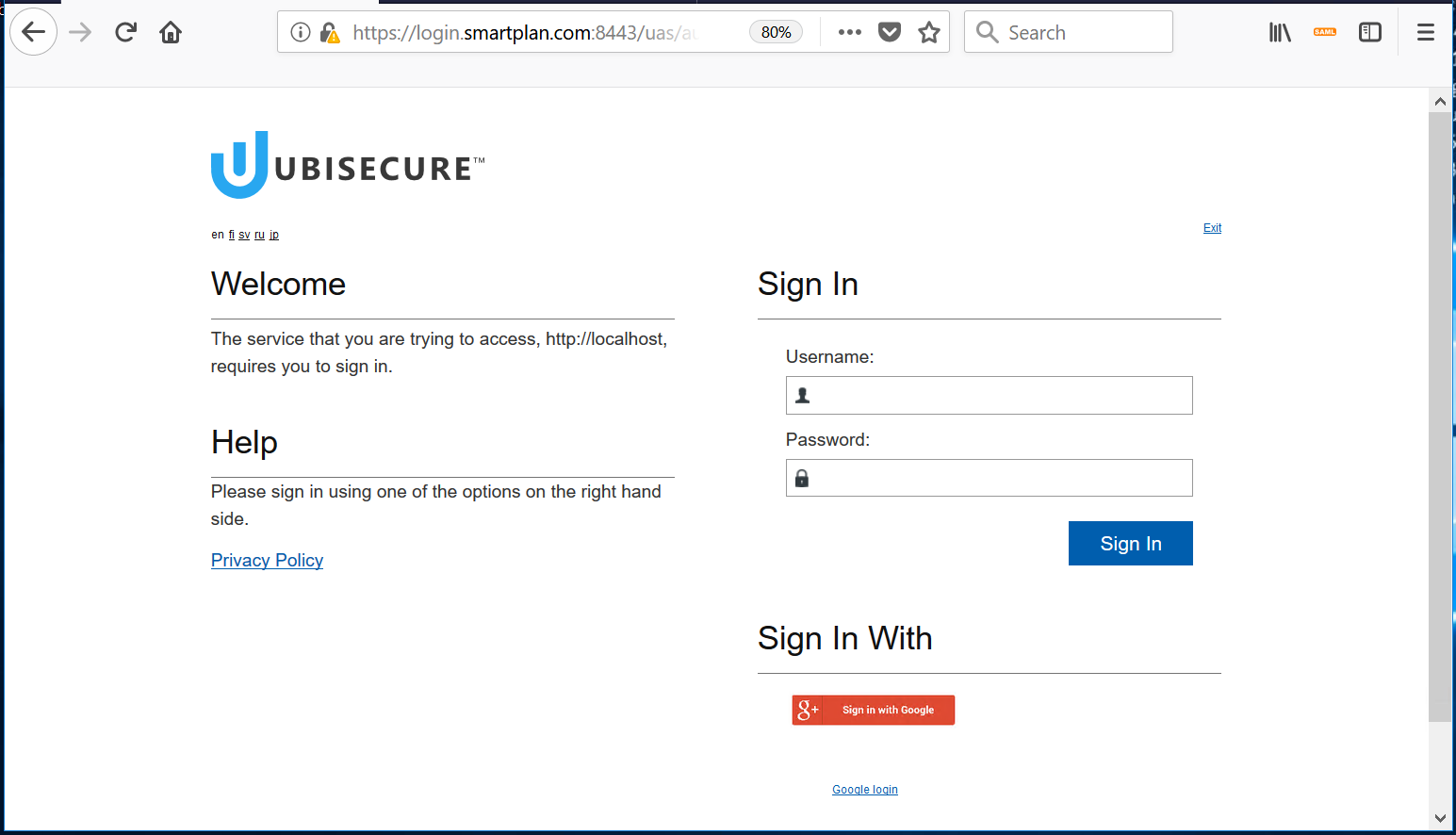
When a user attempts to access a resource protected by Ubisecure:
1. The user enters a username and password and presses next
2. An SMS message is sent to the user’s mobile phone containing an eight digit one-time password
3. The user enters the one-time-password and presses next
4. Authorisation is performed according to the configuration of the Ubisecure SSO Server and the user is redirected to the target application and granted access if permitted
The user’s telephone number is retrieved from the user account stored in the local Ubisecure Directory or in an external directory (AD, LDAP or SQL).
Step 1: Configure SMS OTP on SSO
SMS OTP method is partly pre-configured on your SSO environment.
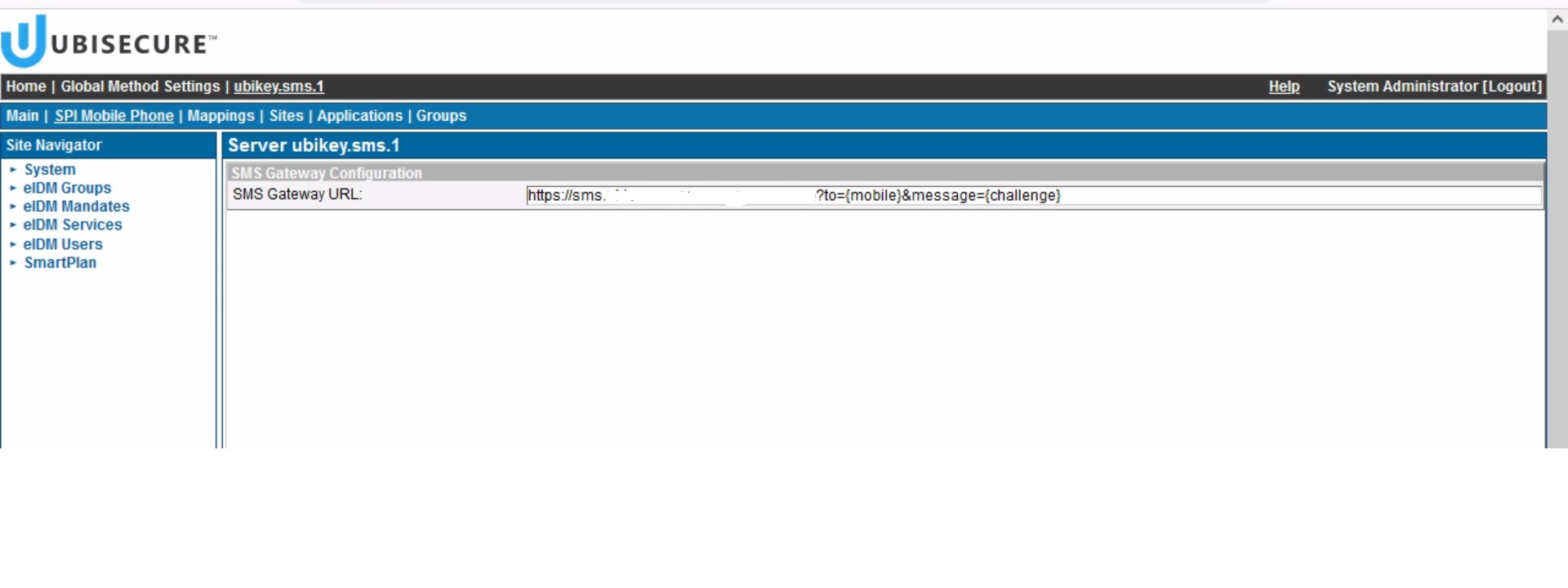
- Go to Global Method Settings and open SMS method. Click "SPI Mobile Phone" tab. You will see the URL of the SMS service, which will look something like this: https://sms.ubisecure.com/smszoner2.asp?to={mobile}&message={challenge}
Open the link and test that you can receive a SMS on your mobile phone. Note that + prefix must be given as URL encoded (%2B).
Test Messagehttps://XXXXXXXXX?to=%2B3584056277673&message=Test
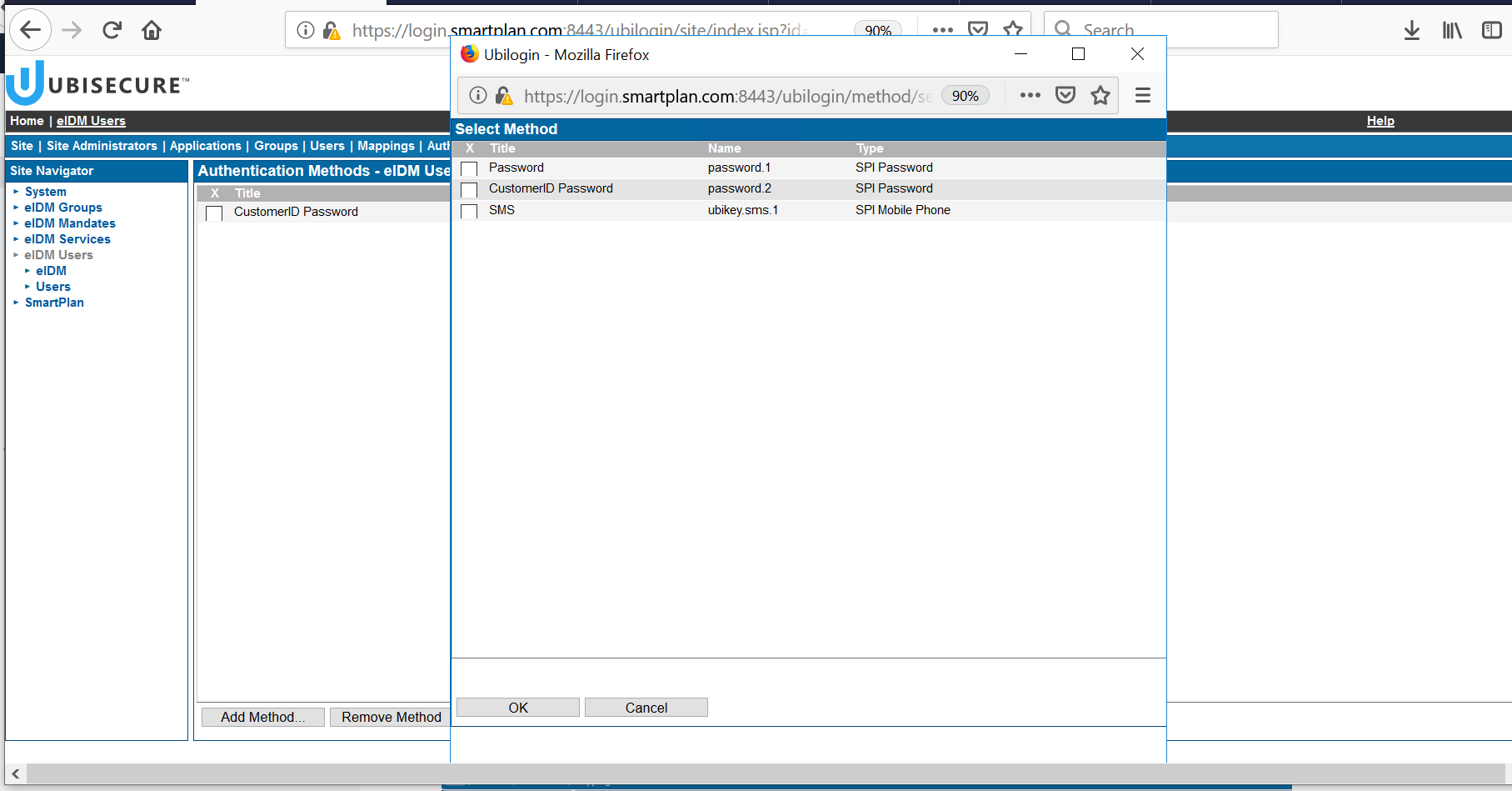
- On SSO Management console, add SMS as authentication method on the SmartPlan site.
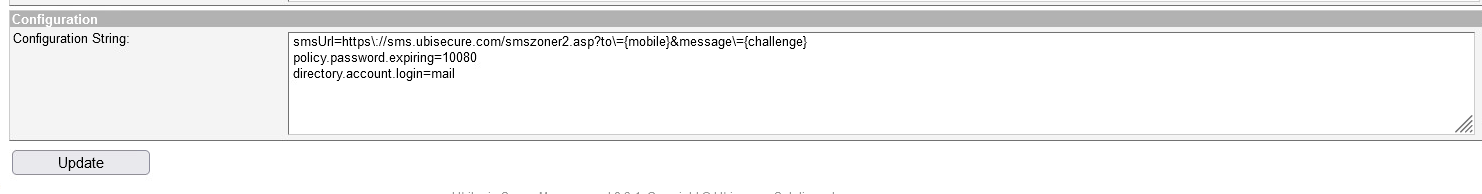
Select the site "SmartPlan", Site Methods, and select Add Methods... and choose ubikey.sms.1 authentication methods that will need to be used on this site. - In order to login using email address, you must add
directory.account.login=mailto the ubikey.sms.1 configuration string. In Global Method Settings, select SMS. Add the string and click the Update button. - Restart UbiloginServer in order the changes to take effect. This must be done after configuring authentication methods.
Step 2: Configure SMS OTP on CustomerID
On CustomerID you must edit eidm2.properties file.
- Open template version of the file C:\Program Files\Ubisecure\customerid\tools\examples\custom\template_eidm2.properties
Search for "# SMS gateway"
# SMS gateway # - This property defines the URL for the SMS gateway. The URL will be used as is, except for # substituting {mobile} and {challenge} for the mobile number and the challenge to be sent by SMS # to the mobile number, respectively. # - Default: <not defined> # - Example: methods.sms.gateway = https://sms.ubisecure.com/smszoner2.asp?to={mobile}&message={challenge}- Copy all the configuration lines above to your working eidm2.properties file in C:\Program Files\Ubisecure\customerid\application\custom\eidm2.properties
Add the following lines to eidm2.properties file
methods.sms = ubikey.sms.1 methods.protected = methods.password, methods.sms
Restart Wildfly
Step 3: Test that SMS OTP is working
If you have configured your SAML application (during Lab 1.2), you can test SMS OTP now. Otherwise leave this for later.
First of all, configure SMS OTP for your sample application "SmartPlan Application"
To configure, on SSO Management console:
- Go to "SmartPlan" site and select Applications tab
- Open sample application (SmartPlan application)
- Select Methods tab
- Uncheck method ”password.2”
- Check method ”ubikey.sms.1” and click Update
Now let's test to verify that SMS OTP authentication is working as expected:
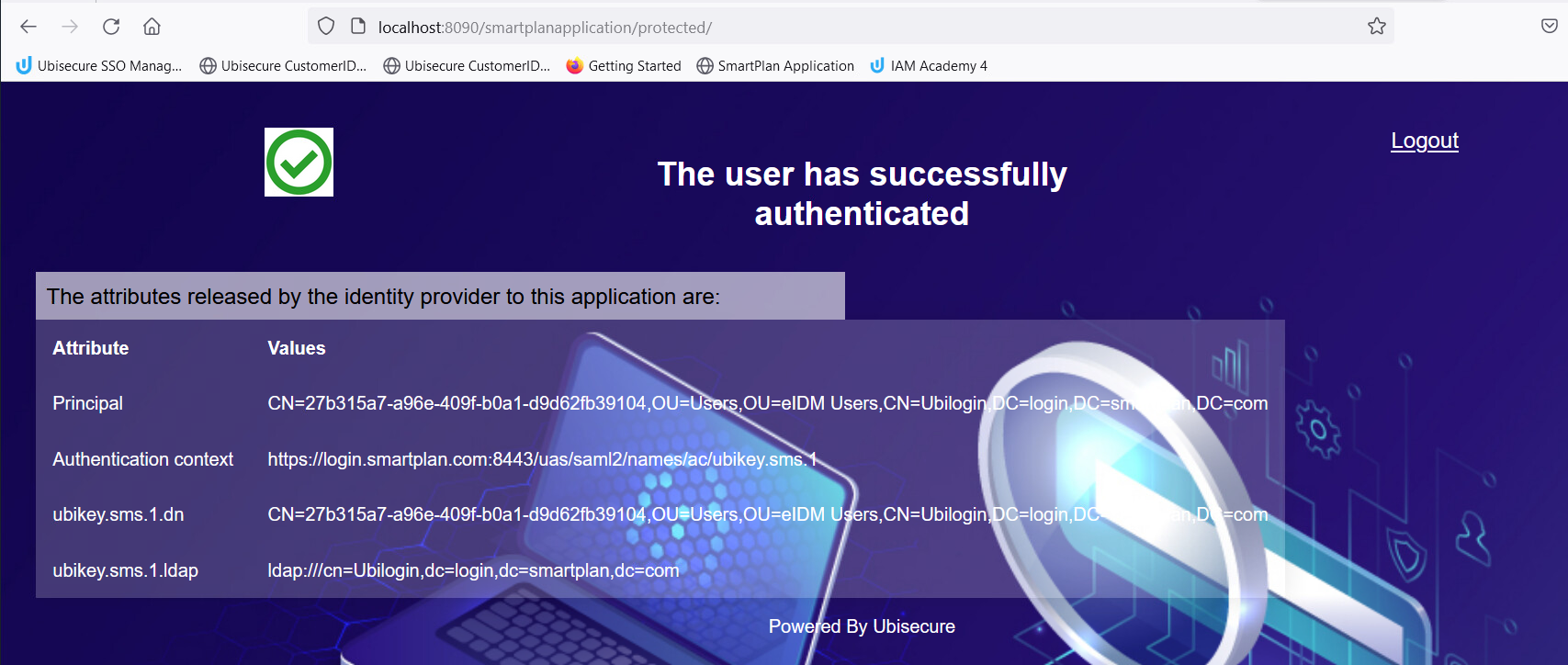
- Go to your sample application (SmartPlan Application): http://localhost:8090/smartplanapplication/ (correct it with the exact URL of your installed sample application, if needed)
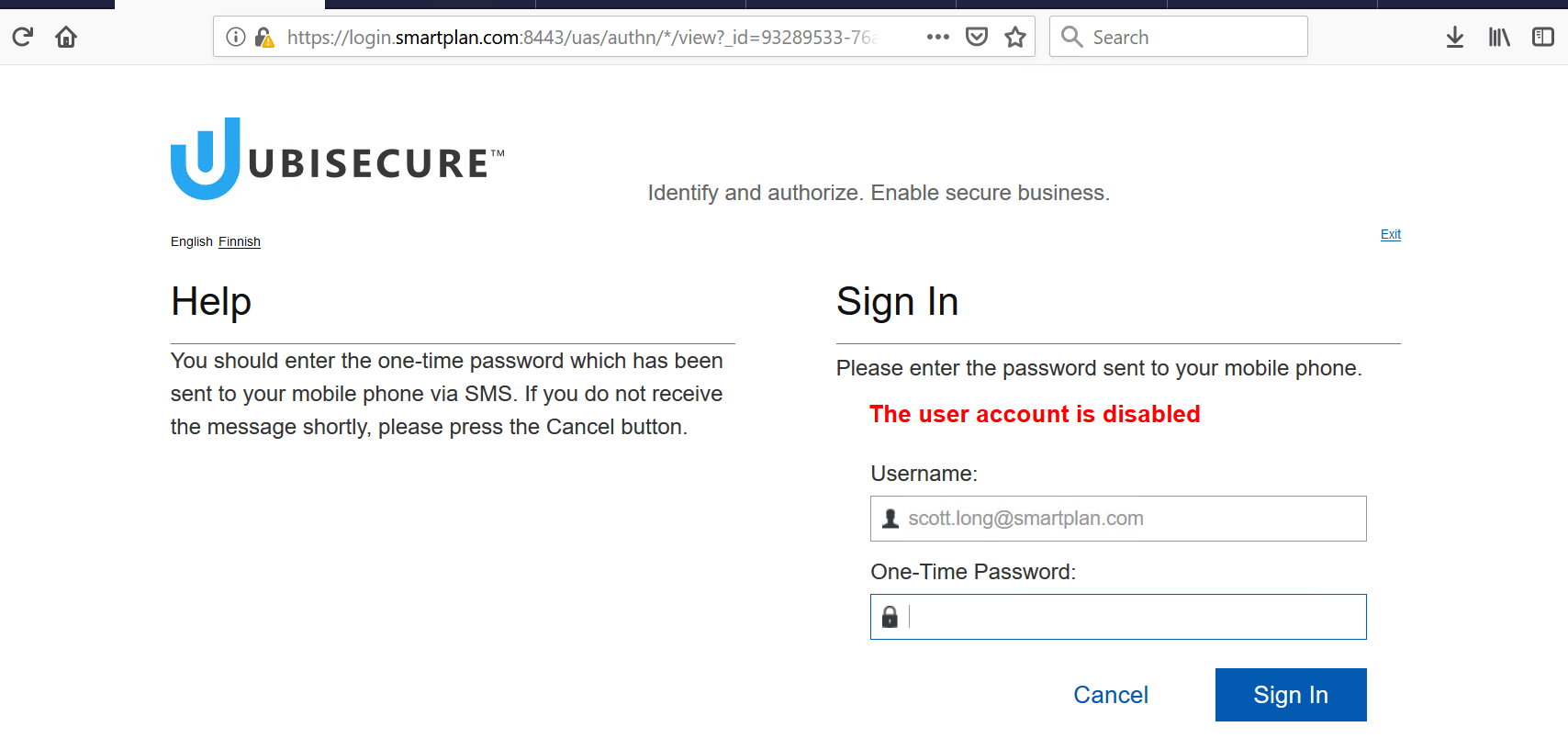
- Log in as Scott Long. user = scott.long@smartplan.com ; password = Password2 and verify that the authentication is interrupted, because you have no mobile number in your user profile.
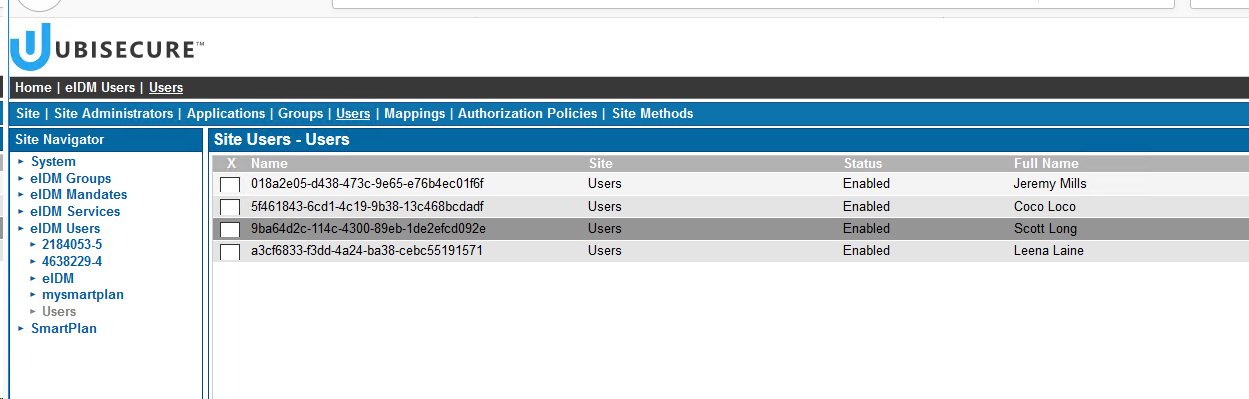
- Go to Ubisecure SSO management. Add ubikey.sms.1 to Site Methods of "eIDM Users" site.
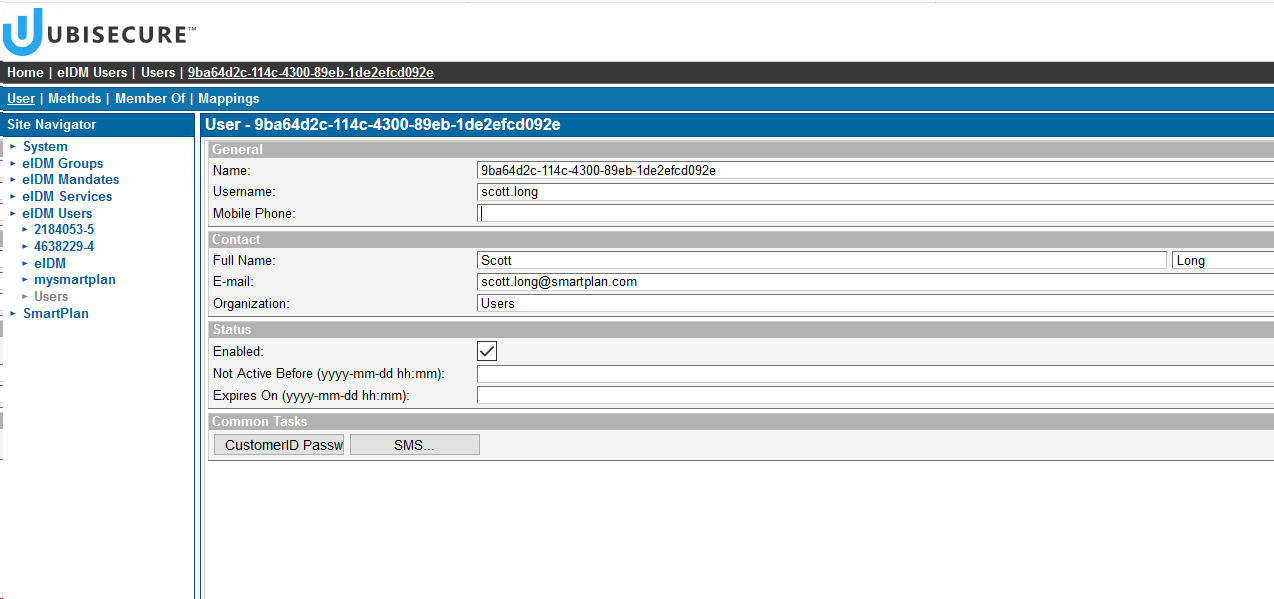
- Then open user Scott Long in eIDM Users / Users. On "Methods" tab activate authentication method ubikey.sms.1
- On "User" tab add your phone number to Scott Long.
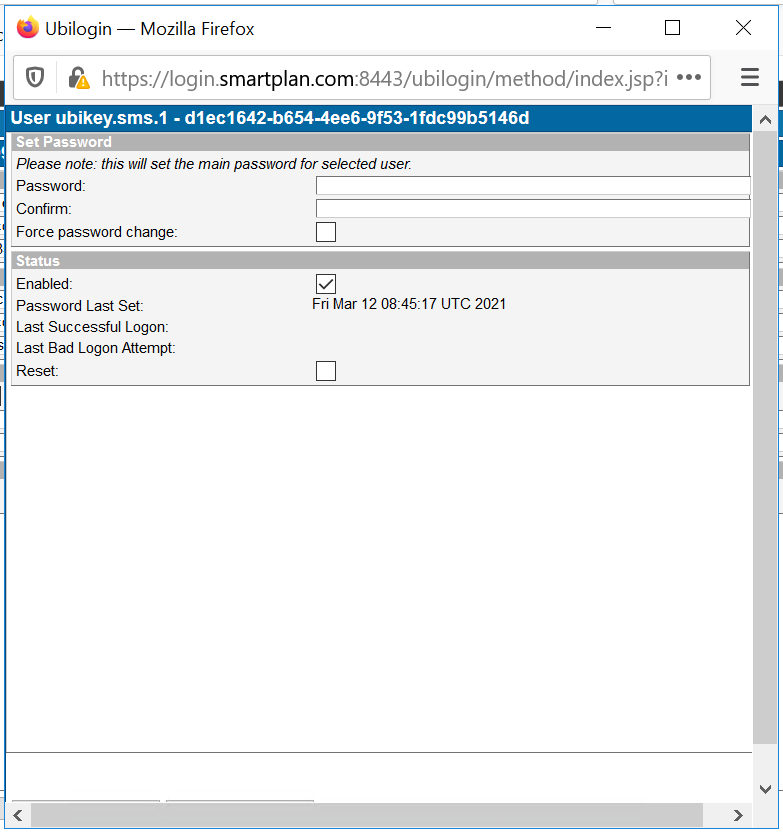
- Click "SMS" and enable the method for Scott Long
- You are ready now. Finally, log into SmartPlan application, and verify that you authenticate with SMS OTP.
- Once you have verified that SMS OTP works as expected, enable password authentication (password.2) again for smartplanapplication. This will be needed in later exercises.
Part 2: Configuring authentication via Social Login for MySmartPlan
You can configure authentication using the credentials of your favorite social media. Ubisecure supports most of services that use OAuth2.0 such as Facebook, Google, LinkedIn and others. General parameters for selected OAuth 2.0 Identity Providers - SSO
Follow the instructions in this knowledge base article to configure Google login:
Configure Google login via OAuth2
Obs: Steps 22 and 24 are not needed as you already configured a SAML sample application (during Lab 1.2). Stop at step 33.
"Applications site" is SmartPlan on your environment
"sample" is SmartPlan Application on your environment