CertAP clustering requirements - SSO
This page specifies the requirements for clustered deployment of Certificate AP. The scope of the Certificate Authentication Provider - SSO pages include the overall deployment architecture, requirements for SSL accelerator and load balancer, and requirements for Certificate AP configuration.
Prerequisites
Competence in the following technologies is required for deploying an Certificate AP cluster:
- Application server clustering (for example, Bea Weblogic Server)
- Load balancer
- SSL accelerator
- Certificate AP installation and configuration
- Ubisecure Server configuration: Certificate AP integration
Clustering Goals
The pursued goals affect the choice of clustering algorithms and deployment architecture. The possible goals of clustering Certificate AP are the following:
- High Availability
The system remains available despite a failing node. Improved availability is achieved using active/active or active/passive clustering. - High Performance
The system is able to serve more clients in a time unit. Improved performance is achieved using active/active clustering. - Maintainability
The system may be upgraded without a service break, upgrading a node at a time. This is achieved using active/passive clustering.
Deployment Architecture
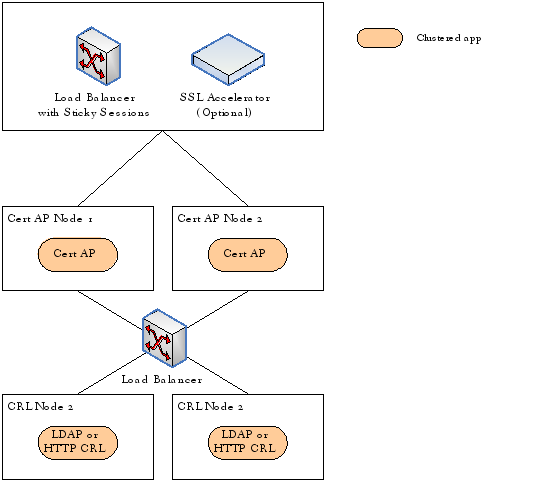
Both high availability and high performance are important for Certificate AP deployment. Therefore, it is recommended to use active/active clustering technique. Such deployment architecture is presented in Figure 1, in which Certificate AP is deployed as a load balanced cluster on two servers with identical configurations. Load balancer is configured to utilize sticky sessions, routing all requests in the same session to the same node.
Figure 1. Deployment architecture of a Certificate AP Cluster |
Deployment Requirements
This section describes the general guidelines for Certificate AP cluster installation and the deployment requirements for time synchronization, SSL accelerator, load balancer, and Certificate AP configuration.
NTP
NTP (Network Time Protocol) must be used to synchronize the clocks of all nodes in the system.
SSL Accelerator
Requirements:
- two-way SSL authentication
- ability to forward the client certificate in an http header to the Certificate AP
The SSL accelerator must be configured to use two-way SSL authentication. The trusted certificate authorities for client authentication should be selected to match the configuration of the Certificate AP.
SSL accelerator must set the client certificate in an http header. Name of the header is configured in web.xml of Certificate AP. An example of such configuration follows:
<context-param> <param-name>com.ubisecure.saml2.uap.client-certificate-header</param-name> <param-value>client-certificate-header-name</param-value> </context-param>
To prevent the user reauthentication after the smartcard is removed, it is recommended to disable the SSL session caching. Also, the connection keep-alive should be disabled or set to a short term. If the SSL accelerator provides the SSL session-id in an http header, Certificate AP is able to block the reauthentication in case of keep-alive. An example of the web.xml configuration block follows:
<context-param> <param-name>com.ubisecure.saml2.uap.session-id-header</param-name> <param-value>session-id-header-name</param-value> </context-param>
Load Balancer
Load balancer must support sticky sessions meaning that all requests in the same session are routed to the same node. This reason for this requirement is the locally stored list of used SSL session IDs.
Certificate AP
Configurations must be identical in both Certificate AP nodes. Therefore, the configuration should be completed on a single node first and then copied to the other node. Installation procedure of the first node is exactly the same as in the single node deployment. Please follow the installation instructions provided on the page Certificate Authentication Provider - SSO.