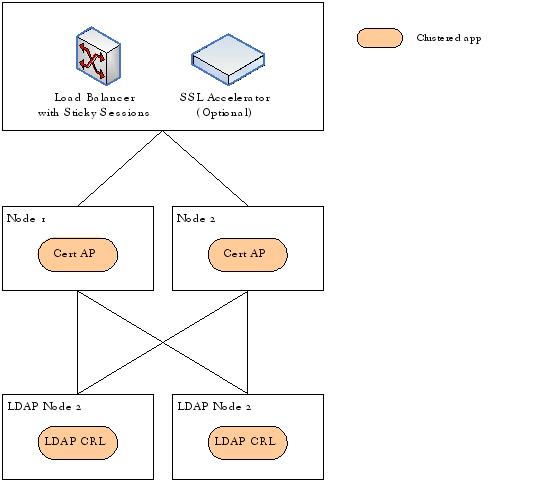
CertAP - client side CRL failover - SSO
Typically a CRL service is clustered at the network level using LDAP or a clustered HTTP CRL. In special cases, if an LDAP CRL service is not clustered in a failsafe manner, client side failover can be enabled and used. The end result is shown below.
| Figure 1. Certificate Authentication Provider with Client side LDAP CRL failover |
To enable the above configuration, use the model policy.xml file shown below in Listing 1. In the model configuration file, the CRL is stored at the addresses ldap://ldap1.fineid.fi:389 and ldap://ldap2.fineid.fi:389. The trusted certificate root has been truncated in the example.
The setting "java.naming.ldap.attributes.binary" forces the nominated attribute to be returned to binary format. This improves compatibility with older non-standard LDAP services, such as Netscape Directory Server 6.21, which does not by default return CRL information in binary format.
Client side failover of CRL lists as a HTTP resource is not supported. Use a standard configuration with standard HTTP load balancing techniques at the network level.
<?xml version="1.0" encoding="iso-8859-1"?>
<Policy
xmlns="http://ubisecure.com/schema/certagent.xsd">
<PKI>
<Trust>
MIIFjDCCBHSgAwIBAgIDAYiZMA0GCSqGSIb3DQEBBQUAMI///certificate truncated
</Trust>
<CRL uri="ldap://ldap.fineid.fi:389/cn%3dVRK%20CA%20for%20Test%20Purposes,ou%3dTestivarmenteet,o%3dVaestorekisterikeskus%20TEST,dmdName%3dFINEID,c%3dFI?certificateRevocationList??objectClass=cRLDistributionPoint">
<Property name="java.naming.factory.initial">com.ubisecure.util.ldap.jldap.JLDAP</Property>
<Property name="java.naming.security.authentication">none</Property>
<Property name="com.ubisecure.util.ldap.server.list">ldap://ldap1.fineid.fi:389 ldap://ldap2.fineid.fi:389</Property>
<Property name="java.naming.ldap.attributes.binary">certificateRevocationList</Property>
</CRL>
</Trust>
</PKI>
<Subject KeyInfoConfirmationData="true"/>
<Attributes>
<Add name="username">
<Digest source="subject" algorithm="sha1" />
</Add>
<Add name="username.dn">
<Field source="subject"/>
</Add>
<Add name="ais">
<Field source="subject" normalize="altSecurityIdentities"/>
</Add>
<Add name="satu">
<Attribute source="subject" oid="2.5.4.5"/>
</Add>
<Add name="username.name">
<Concat>
<Attribute source="subject" oid="2.5.4.4"/>
<Text content=" "/>
<Attribute source="subject" oid="2.5.4.42"/>
</Concat>
</Add>
</Attributes>
</Policy>