Configure OpenID Connect Sign in with Apple
The configuration of Apple ID authentication method requires Ubisecure SSO 8.10.x or later
Table of Contents
Step-by-step guide
Prerequisite
Register with Apple ID to obtain client ID (Service ID), client secret, and register redirect URI. Information how to register can be found in Sign in with Apple Developer Documentation.
Note: The redirect URI will be constructed by SSO in the format: https://<sso base url>/uas/return/<method name>/redirect
The <sso base url> must be accessible to the Sign in with Apple servers
Configuration
The method can be configured either through SSO Management Console or SSO Management API. Here you can find instructions for configuration with SSO Management Console. API instructions can be found from the link at the bottom of the page.
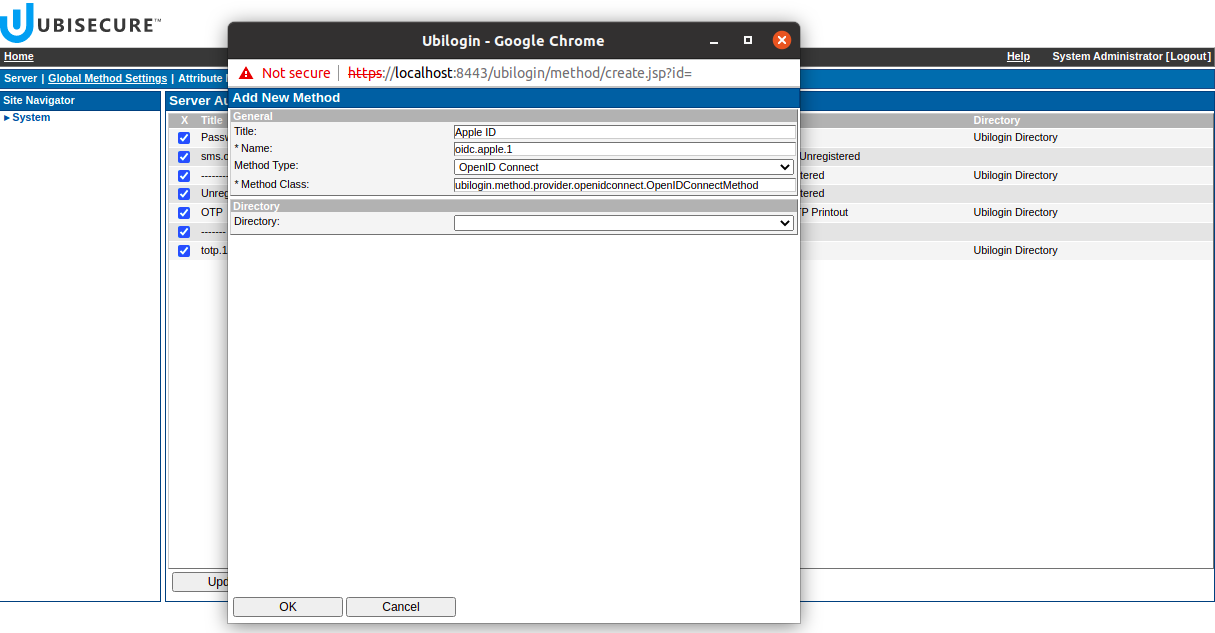
Login to SSO Management Console. Go to Global Method Settings → New method… and create the method. Remember to give the right name to the method as it is in the registered redirect URI.
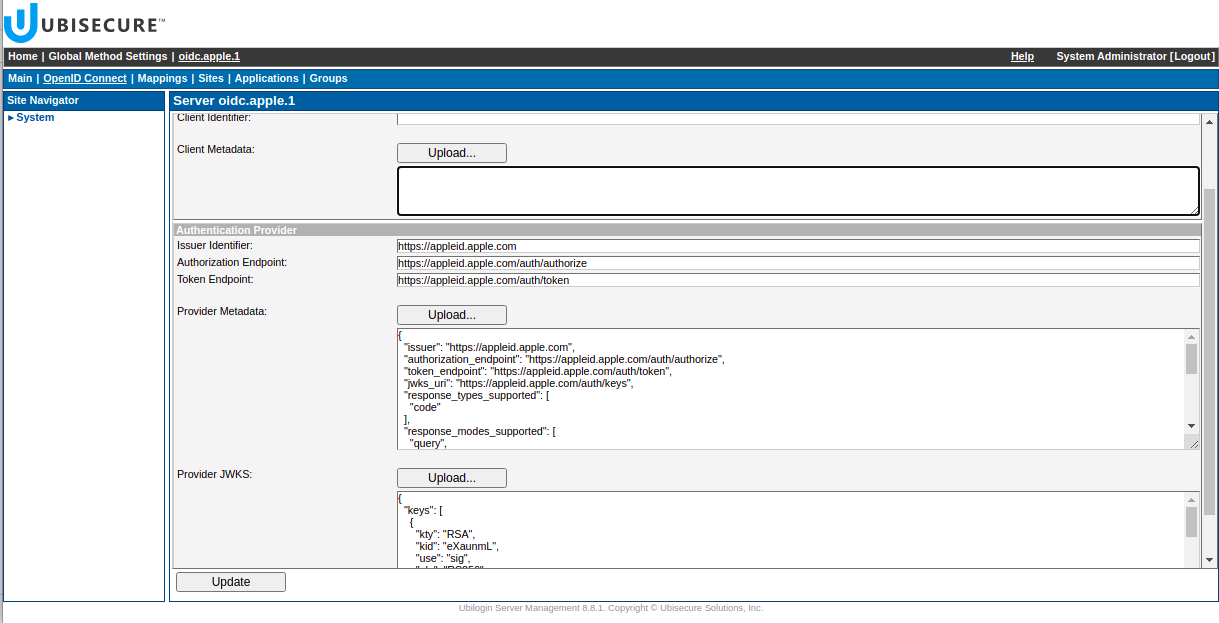
Create new method for Apple OIDC - Go to Open ID Connect tab, and upload the Provider Metadata. Apple ID metadata can be found from here: https://appleid.apple.com/.well-known/openid-configuration
Upload the Provider Keys, which can be found from the
jwks_uriin the provider metadata:Apple OIDC - Authentication Provider configuration - Upload Client Metadata, where you specify your client ID and secret, and define scope, based on the claims you want to receive from Apple ID.
- If you don’t have client metadata already, you can download a template, which can be modified and uploaded:
Press Create next to Registration Request. This will download a JSON file.
- Modify the file based on your needs. Remember to add at least:
- your client ID (Service ID) and secret,
- your redirect URI
- add new attribute
id_token_max_lifetimeset to86400(in order to SSO accept Apple id_token with the lifetime set to 24 hours), add attribute
ubisecure_request_parametersto defineresponse_modeasform_post:Client metadata for Apple example{ "client_id": "<client id>", "client_secret": "<client secret>", "redirect_uris": [ "https://<sso base url>/uas/return/<method name>/redirect" ], ... "id_token_max_lifetime": 86400, "ubisecure_request_parameters": { "response_mode":"form_post" }, ... }
- Upload the file as Registration Response or Client Metadata.
If you have your client metadata, you can simply upload it by clicking Upload next to Client metadata.
- You should see your client ID as Client identifier and a new field Client secret (already set).
- If you don’t have client metadata already, you can download a template, which can be modified and uploaded:
Press Update.
Apple OIDC method configuration Go to Main tab, select Enabled box and add configuration strings:
Compatibility=AppleId OperationMode=private
and press Update.
Apple method settings - enabling and configuring - The configuration of the method is now done. Next you need to add it to your application.
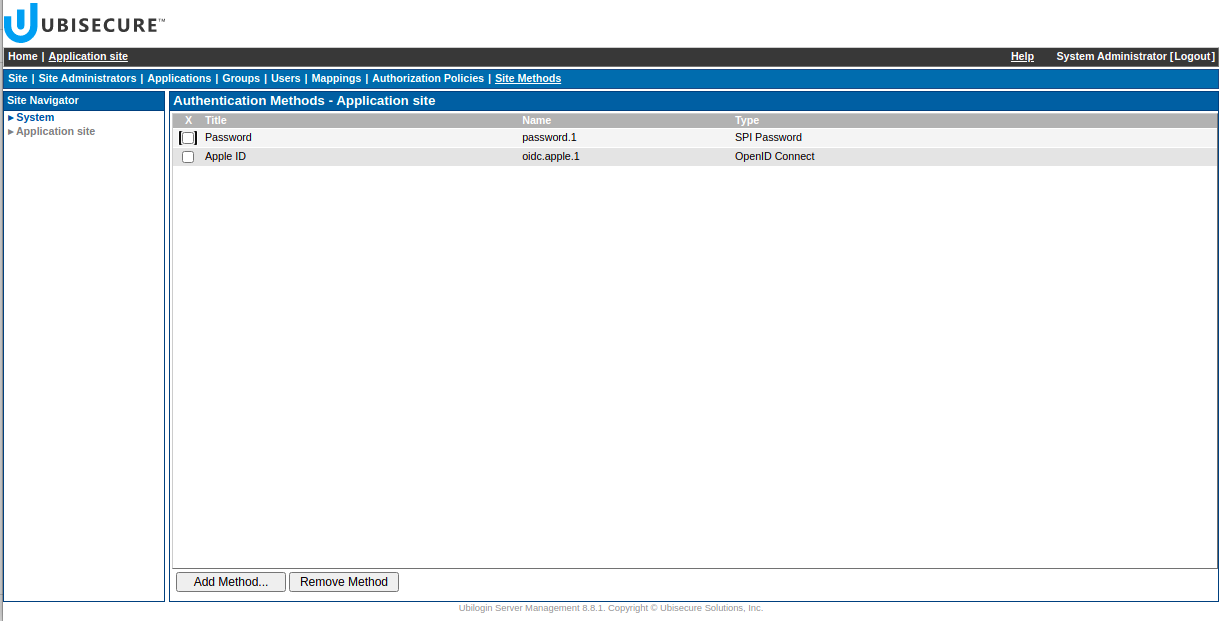
First, add the method on site level of your application. Go to Site methods → Add method... and choose “Apple ID” method.
Add Apple method to the site methods - Create a dynamic group for access control, where membership is based on the authentication method used to log in. In the site view, go to Groups → New Group..., and create a group, e.g “Apple ID users”. Then, in the group view, go to Allowed Methods tab, select the authentication method “Apple ID” and press Update.
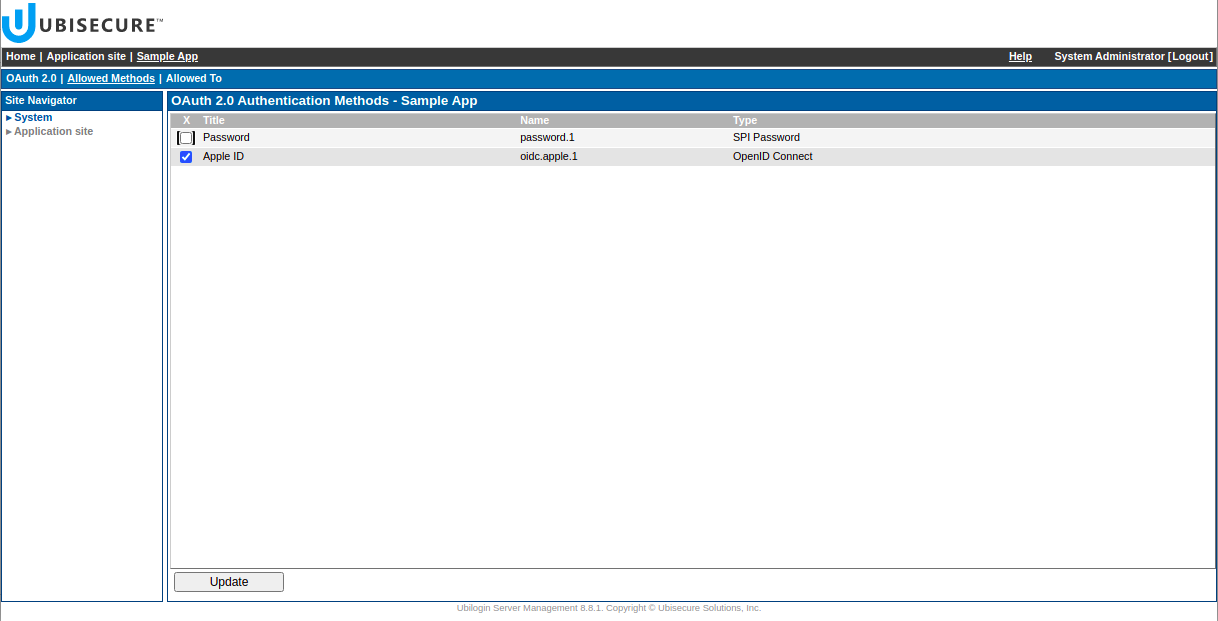
Go to your application and in Allowed Methods tab select “Apple ID” method and press Update.
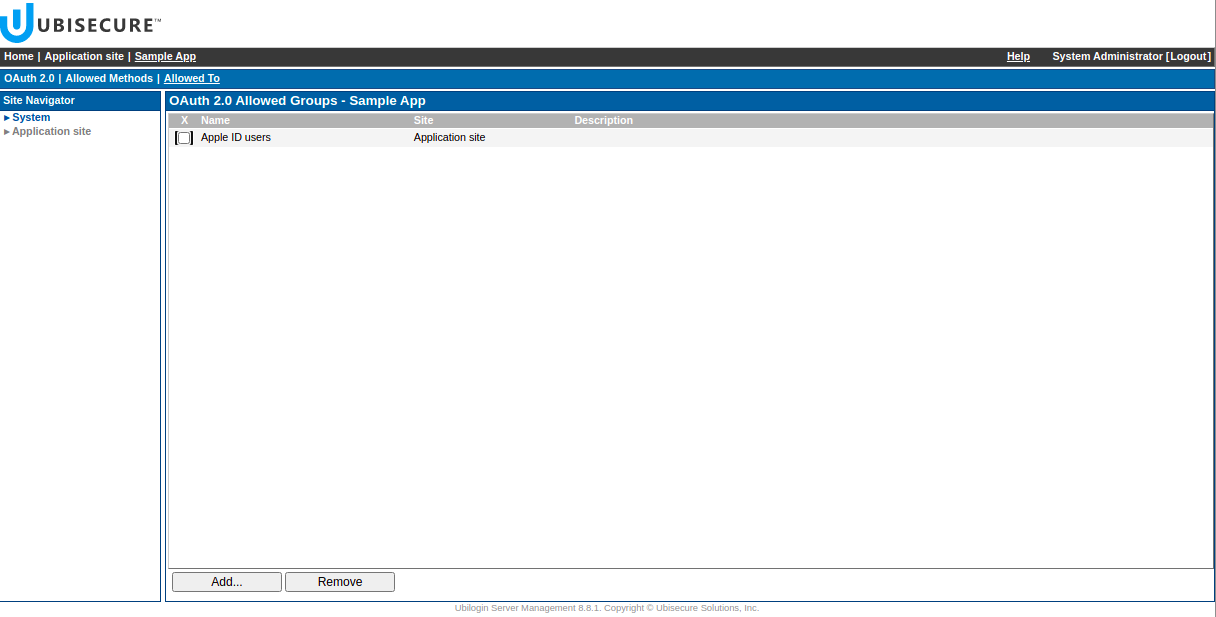
Add Apple method to the Allowed Methods of the application Go to the Allowed To tab, press Add... and add the group “Apple ID users”.
Add the group created in step 9 (associated with Apple method) to the allowed for the application - Since Apple OIDC uses
response_mode=form_post, cross-domain communication occurs. Google Chrome (version 80 and higher) has changed its default cookie behavior. To ensure proper communication between different top-level domains, please take the following actions described in our SameSite cookies changes technical announcement. - Now the configuration is done, users should be able to log in using Apple ID to your application.
Additional links
OpenID Connect authentication method
Configuring authentication method's logo
SameSite cookies changes technical announcement